Modules 16 17 building and securing a small network exam – Modules 16-17 Building and Securing a Small Network Exam provides a comprehensive exploration into the fundamentals of network security, empowering readers to safeguard their networks against potential threats. This module delves into the essential components of network infrastructure, their configurations, and the implementation of robust security measures.
As networks become increasingly complex and interconnected, the need for effective security practices has never been more critical. Modules 16-17 provide a practical framework for understanding network security concepts, enabling readers to build and maintain secure networks that meet the demands of modern business environments.
Building a Small Network
Building a small network involves designing a network diagram, identifying hardware components, and configuring each component for optimal performance and security. A well-designed network provides reliable connectivity, efficient data transfer, and enhanced security.
Network Diagram
A network diagram is a visual representation of the network topology, including devices, connections, and protocols. It helps in planning, troubleshooting, and maintaining the network. The diagram should include:
- Network devices (routers, switches, firewalls)
- Physical connections (cables, wireless links)
- Network protocols (TCP/IP, UDP)
Hardware Components, Modules 16 17 building and securing a small network exam
The hardware components of a small network typically include:
- Routers:Connect different network segments and provide internet access.
- Switches:Connect devices within a network segment.
- Firewalls:Protect the network from unauthorized access and malicious traffic.
- Wireless access points:Enable wireless connectivity for devices.
Component Configuration
Each network component must be configured for optimal performance and security. This includes:
- Router configuration:Assigning IP addresses, setting up routing protocols, and configuring security features.
- Switch configuration:Setting up VLANs, configuring port security, and managing traffic flow.
- Firewall configuration:Defining access control rules, enabling intrusion detection and prevention systems, and managing security policies.
- Wireless access point configuration:Setting up SSIDs, configuring encryption, and managing channel selection.
Securing a Small Network: Modules 16 17 Building And Securing A Small Network Exam
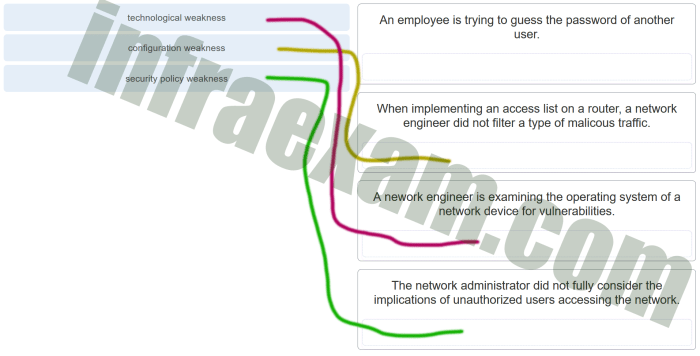
Securing a small network involves implementing various security measures to protect against unauthorized access, malicious attacks, and data breaches. These measures include:
Firewalls
Firewalls are network security devices that monitor and control incoming and outgoing network traffic. They enforce access control policies, block unauthorized connections, and prevent malicious traffic from entering the network.
Intrusion Detection and Prevention Systems (IDS/IPS)
IDS/IPS systems monitor network traffic for suspicious activities and security threats. They can detect and block malicious traffic, such as malware, viruses, and hacking attempts.
Access Control Policies
Access control policies define who can access network resources and what they can do with them. These policies can be implemented using authentication mechanisms, authorization rules, and role-based access control (RBAC).
Network Security Threats and Mitigation
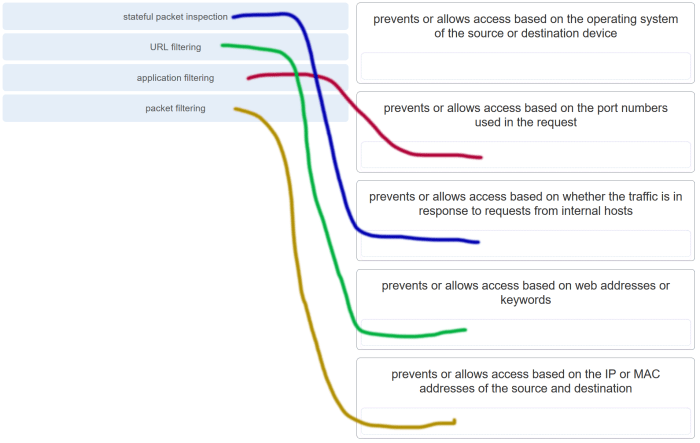
Small networks face various security threats, including:
- Malware:Malicious software that can damage or steal data.
- Phishing:Emails or websites that trick users into revealing sensitive information.
- Hacking:Unauthorized access to network resources or data.
- Denial-of-Service (DoS) attacks:Overwhelming a network with traffic to make it unavailable.
To mitigate these threats, small networks should implement:
- Anti-malware software:Detects and removes malicious software.
- Phishing awareness training:Educates users about phishing techniques.
- Strong passwords and multi-factor authentication:Makes it harder for attackers to gain unauthorized access.
- Network segmentation:Divides the network into smaller segments to limit the impact of security breaches.
Network Monitoring and Troubleshooting

Network monitoring is essential for detecting and resolving network issues. It involves:
- Monitoring network performance:Using tools to track network traffic, bandwidth utilization, and device health.
- Identifying and resolving network problems:Troubleshooting common issues such as slow performance, connectivity problems, and security breaches.
- Implementing proactive maintenance:Performing regular maintenance tasks to prevent network outages and improve performance.
Best Practices for Network Management
Best practices for network management include:
- Network design and configuration:Following industry standards and best practices for network design and configuration.
- Network management plan:Creating a comprehensive plan for network management, including security policies, maintenance procedures, and disaster recovery plans.
- Network optimization:Continuously monitoring and optimizing network performance to improve efficiency and reliability.
Questions Often Asked
What are the common network security threats?
Common network security threats include malware, phishing attacks, unauthorized access, denial-of-service attacks, and man-in-the-middle attacks.
How can I mitigate network security threats?
Network security threats can be mitigated through implementing firewalls, intrusion detection and prevention systems, access control policies, and regular security updates.
What are the best practices for network management?
Best practices for network management include regular network monitoring, proactive maintenance, network segmentation, and implementing security policies.